

What must you do with these? Nothing. The book files are not encripted, you can download and use them freely under the Creative Commons license cited. You need never obtain any digital signature files or pay them any attention whatsoever
What can you do with digital signature files? To be honest, I can't think of a strong use case for them. The idea is that they are proof of my authorship, and that the signed file is 'as shipped', byte for byte. How this works is as follows.
Why didn't I embed each certificate in its subject file? This seemed such a mess to me — import this, convert that. Since GnuPG is available on several platforms, the simplest approach was just to use it. File, certificate, there you go.
I give instructions below for using GnuPG to verify any file for Linux and Windows.
gpg --import johnmckellar.gpg.txt
gpg --verify B1H_vol1-1.0.pdf.sig
You should see output as follows:
gpg: assuming signed data in `B1H_vol1-1.0.pdf' gpg: Signature made Sat 23 Apr 2022 22:52:35 CEST using RSA key ID DAA73675 gpg: Good signature from "John McKellar <jdm.b1h.author@gmail.com>" gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner. Primary key fingerprint: 68D2 C8AD A095 5818 C484 872E F226 8703 E101 BF9BThe third line is the important one. If the file and the signature don't match, you will see output like the following:
gpg: assuming signed data in `B1H_vol1-1.0.pdf' gpg: Signature made Sat 23 Apr 2022 22:52:35 CEST using RSA key ID DAA73675 gpg: BAD signature from "John McKellar <jdm.b1h.author@gmail.com>"So why the warning? For an explanation, try this page in the GnuPG Manual. Basically, you can get rid of it by declaring my key 'trustworthy'. I just don't see what the point of this is. So my advice is simply to ignore this somewhat spurious warning.
Ok so you are going to want to step through the following procedure.
You are all set then to verify the pairs of file/signature which you can download from my book sites. For each of these .sig files, you can do that as follows:
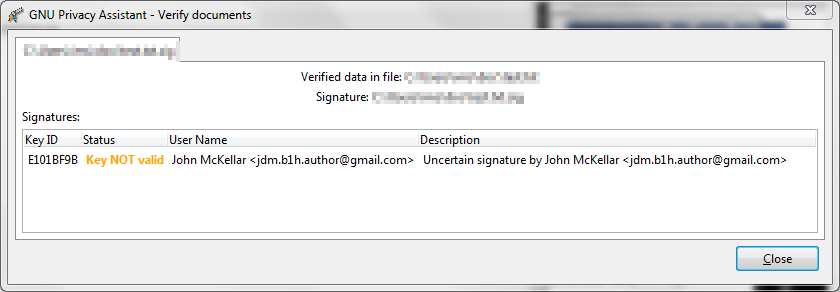
Oh no! Looks like the signature is no good!
No. This is the same issue as gave you the warning if you use Linux. See again this page in the GnuPG Manual. Actually, the signature is ok. I really don't think we need to get into levels of trust and so forth. It's just a book, not a pass to get you into Fort Knox.
If the signature really was bad, you'd see this:
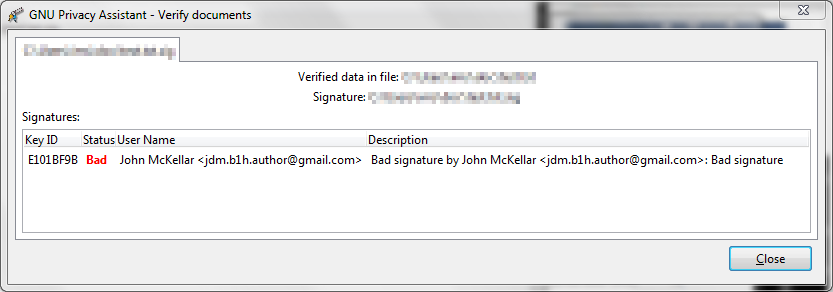
Note that you can also do all of this with identical commands to Linux if you use Window's command-line utility.